Offshore teams have become a vital part of modern business operations, enabling companies to tap into global talent pools while reducing costs. However, distributing workforces across multiple locations introduces complex cybersecurity challenges that cannot be ignored. From endpoint vulnerabilities to compliance requirements such as SOC 2 and GDPR, organizations must implement comprehensive strategies to safeguard sensitive data (Compliancy Group, 2024).
This article explores real-world breach examples, practical cybersecurity controls, compliance frameworks, and cultural approaches to building trust in global workflows — all with the goal of equipping leaders with actionable insights to secure offshore teams.
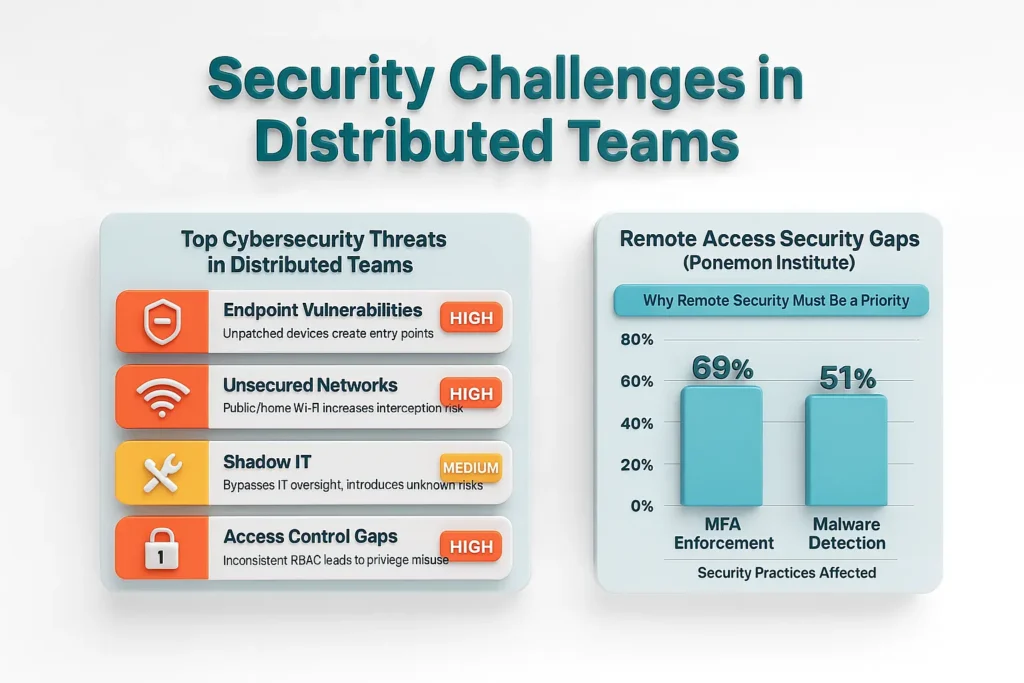
In a traditional office environment, network access and device use are controlled within a central perimeter. Offshore teams, however, operate from diverse geographies, networks, and devices, which significantly expand the attack surface (SBS Cyber, 2025).
Common challenges include:
Unpatched operating systems and outdated applications on offshore employee devices create exploitable entry points.
Home Wi-Fi without WPA3 encryption or the use of public networks increases the risk of man-in-the-middle attacks.
Unauthorized use of unapproved SaaS tools that bypass IT oversight.
Gaps in enforcing role-based access and least-privilege principles across jurisdictions.
A Ponemon Institute study found that 69% of organizations do not enforce multi-factor authentication (MFA) for remote access and 51% have experienced malware bypassing intrusion detection systems (Ponemon Institute, as cited in Compliancy Group, 2024). These statistics underscore why distributed team cybersecurity must be treated as a priority, not an afterthought.
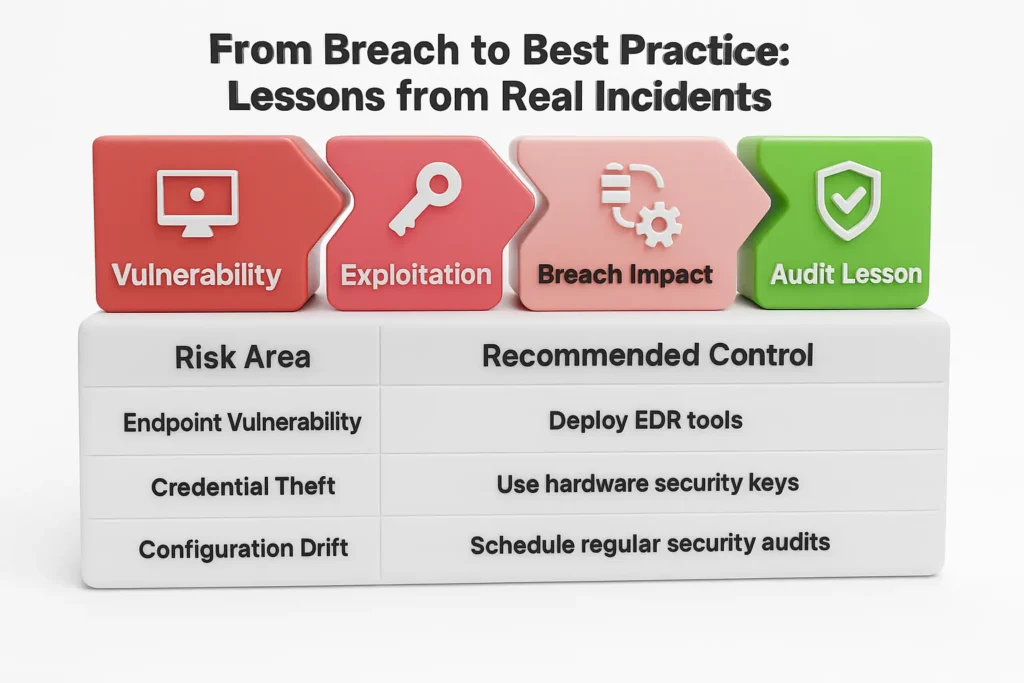
The 2022 LastPass breach is a well-documented case of how offshore or remote security gaps can lead to major incidents. Attackers exploited a compromised endpoint belonging to a DevSecOps engineer, gaining access to encrypted password vaults and sensitive metadata (Gentles et al., 2025).
Key lessons from this and similar breaches include:
Similarly, in offshore hiring scams reported by penetration testing firm Covertswarm (2025), criminals impersonated legitimate job applicants to gain access to sensitive internal systems. This reinforces the importance of identity verification in the onboarding process for offshore hires.

Effective security controls form the backbone of protecting offshore workflows. Industry best practices include:
Offshore team members should only have the permissions required for their current role (Vocal Media, 2024).
IAM solutions should enforce role alignment with automatic access revocation upon role change or contract termination (InsourceIndia, 2025).
Full-disk encryption, EDR solutions, and enterprise-grade anti-malware should be standard (GDPR.eu, n.d.).
Requiring the use of VPNs or virtual desktops to eliminate local data storage and control network traffic paths.
Using encrypted channels and disabling public link sharing for sensitive files.
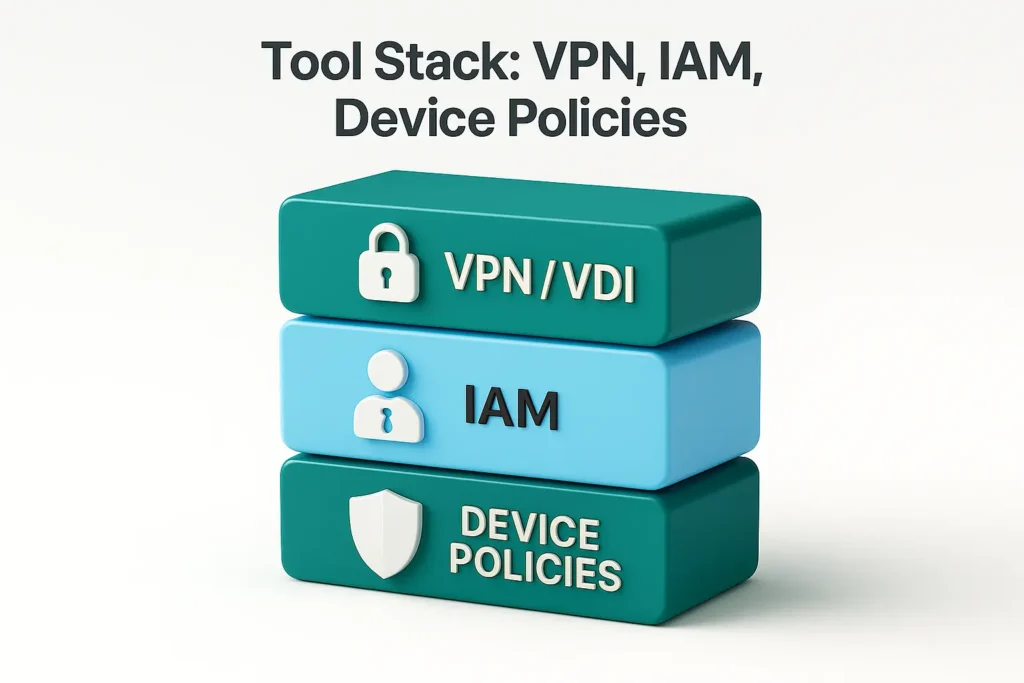
Building a robust security tool stack ensures consistent application of policies across offshore teams:
Device Management Policies – Mandating encryption, auto-patching, and mobile device management (MDM) solutions to maintain endpoint compliance (SBS Cyber, 2025).
Security controls for offshore teams should align with recognized compliance frameworks:
Deliver monthly cybersecurity awareness training (SecurityBlue Team, 2025).

Expand effortlessly with My Offshore Employees - access top 1% offshore talent starting at just $3/hr or $600/month per FTE. No hidden fees, no compromises on quality. Your offshore employees work exclusively for you - ensuring focus, transparency, and real-time visibility into your projects. We combine smart automation and proven industry experience to deliver higher productivity, fewer errors, and tailor-made solutions for your business growth.
© 2025. All Rights Reserved.